- Bellingcat Challenge Newsletter
- Posts
- The Forgotten Files
The Forgotten Files
Uncovering dark secrets buried in time

It’s the first week of July, so we’re back with a new series of challenges and of course, a new newsletter! Last month’s cultural deep dive kept many of you busy, but we hope you’re ready for more. This month we’ll go back in time, to uncover the evidence hidden in open source data from the past.
In this newsletter we’re highlighting a few community members who tackled last month’s challenges in a creative way. Don’t forget to share your work with us if you’re writing about your methods as well! You’ll also find out how our researcher Carlos Gonzales dealt with last month’s tasks later on…

July Challenge - The Forgotten Files
Our researcher Peter Barth doesn’t shy away from a deep dive into complex historical crimes. Recently, we published his investigation into the killing of a Texas oil tycoon over 50 years after his death. Peter worked on this investigation for years, collecting pieces of evidence through public records, FOIA requests and interviews. In collaboration with the Texas Observer, he was able to find fresh leads and shine light on one of the overwhelming number of unsolved homicides in the United States. You can read his investigation here.
Or find the video version of the investigation here:
Peter also presented his work in last week’s stage talk and shared how you can investigate cold cases using open sources. You can listen to this talk’s recording here, it might offer clues relevant to this month’s challenges.
Okay, let’s get going! You can find the latest challenges here. Also, don’t forget to ask for help, share your methods and join the club of people losing their minds over that one impossible exercise. You’re in good company!
This month’s livestream will feature our researcher Jake Godin. Tune in on Wednesday, July 16 at 5 PM CET, to see how he approaches Peter’s cold case exercises. The stream will be available on our Patreon.
June’s Cultural Confusion:
SPOILER ALERT: From this point on, we’ll be discussing last month’s challenges. If you still plan to complete them, you may want to skip this section.
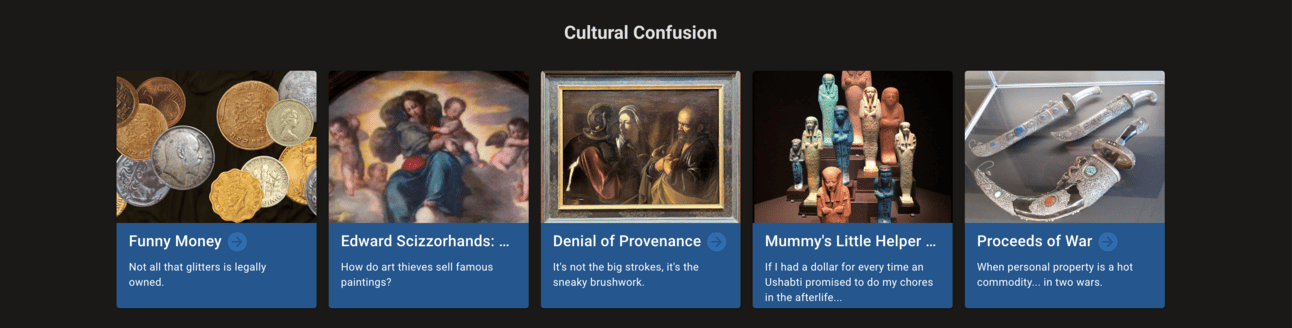
Screenshot of last month’s challenges
From the emperors of the Qing dynasty and Egyptian Ushabti’s to a Nazi art-dealer, June’s challenges were packed with fascinating stories from the team of The Association for Research into Crimes against Art (ARCA). The challenges demonstrate how open source research can contribute to the investigation of art crime and the protection of cultural heritage.
Here are the answers to the “Cultural Confusion” challenges:
Barry H. Berke
Wannenes
Jeu de Paume
Bonhams Semataui
Spanish
We’ve received some amazing write ups and blogs again this month – thanks for everyone contributing. Let’s see what we can learn from them.
Arthur Martins Zimmermann shared on LinkedIn that searching the terms “coin 20$ million 1933” on Google led him to discover that the “double eagle” coin matched all the characteristics described in the “Funny Money” exercise. DamCoffee wrote on their blog that after identifying the coin, they were able to find more about the legal dispute in a SCV History article. While DamCoffee was able to find the full name of the attorney directly in the article, Arthur took a different approach and needed an additional search query to identify Barry H. Berke by name.
B!ns3c found the answer to “Edward Scizzorhands: Art Thief”, by googling “1982 stolen painting piece cathedral”, which led to the story of Federico Barocci’s altarpiece. The piece was stolen in 1982 and rediscovered in 2017. GeoHooper arrived at the same answer through a reverse image search on TinEye. Both blogs described how art dealer Giancarlo Ciaroni was instrumental to find the final answer. Ciaroni recognized the missing piece among the lots listed for an upcoming sale at the Wannenes auction house.
“The denial of provenance” wasn’t an easy challenge. As someone on our Discord server put it: “I've been hitting my head into a brick wall named Ian Dik for hours.” Ian Dik turned out to be part of the solution for many participants, including GeoHooper. In their blog, they explain that Ian Dik is one of the names mentioned in the provenance section of the painting shown in the challenge photo. You can find this on the website of The Metropolitan Museum of Art, where it is currently held.
It’s important to note that the challenge description states that there was a mistake in the provenance. GeoHooper spent hours searching for the family names mentioned in the provenance, until they googled “Dik artwork dealer 1942”. This Google search provided two key insights. Jan Dik had been misspelled as “Ian Dik” in the provenance record, and the search revealed that Dik was known to have traded art with Nazi officials. Searching “Jan Dik 14 may 1942 art deal” led them to a document stating that Jan Dik sold art for prominent Nazi figure Hermann Göring at the Jeu de Paume museum in Paris.
Shiza Hidayet Khan found the same answer by focusing on the date rather than the painting. By combining the date with search terms like “Nazi plunder” and “meeting”, she identified one location that appeared in two separate Wikipedia articles, leading her to the answer.

The provenance record of ‘The Denial of Saint Peter’ on the website of the The Metropolitan Museum of Art.
The fourth challenge was much more straightforward. For “Mummy’s Little Helper”, Shiza Hidayet Khan Googled “Ushabti sold in London in 2013 for £937.50” and found a single result: the auction listing for one of the ushabtis in the picture. The listing mentioned “shabti for Semataui,” indicating that the Ushabti was made to serve Semataui. The listing was on the website of the Bonhams auction house.
In “Proceeds of War”, both GeoHooper and Shiza Hidayet Khan identified the dagger in the challenge photo via reverse image search, which led them to an exhibition in Ukraine. Shiza then searched in Ukrainian to gather more information and came across an article which mentioned the name of the original owner of the dagger, and the historical context that matched with the clues in the challenge. Eventually, she searched for “Henry Pu Yi + dark web”, and found a news article referencing a dark web listing, including the suspected nationality of the seller.
GeoHooper turned to Yandex, a search engine that is especially useful for searching Eastern European and Cyrillic content. On this search engine they found an article that included an official letter from the Security Service of Ukraine. A Yandex reverse image search on the letter image led them to an art crime blog that points to a criminal network operating out of Spain. This blog was also coincidentally written by Lynda Albertson, the author of this challenge!
Curious to see how Bellingcat’s Research lead Carlos Gonzales tackled these challenges? Check out last month’s livestream here:
Don’t want to solve the challenges alone? Of course we have our Discord community, or social media platforms to chat about how you can solve the challenges. But the team of OSINT Switzerland took it to the next level. They organised an event where more than 20 open source research enthusiast took on last month’s Bellingcat challenge together. Great idea to gather some friends and do this in-person!
That’s it for this month’s Bellingcat Challenge newsletter. We’d love to hear your feedback on the challenges. Join us on Discord and let us know if you have ideas for future challenges or things you’d like to see in this newsletter.
If someone forwarded this to you and you’d like to subscribe, you can do that here.
Elsewhere on Bellingcat
Before we go, here are some links to other exciting projects from Bellingcat:
See you next month!
